TrustedSec discovered that Azure Front Door WAF’s IP restrictions can be bypassed when using the default RemoteAddr setting. When the bypass works, ALL WAF rules get disabled - not just IP filtering.
Front Door WAF has a specific fingerprint: 403 responses include both x-azure-ref and x-cache headers. Application Gateway WAF doesn’t include these.
I’ll definitely forget these details in six months. That’s why I wrote this BCheck:
metadata:
language: v2-beta
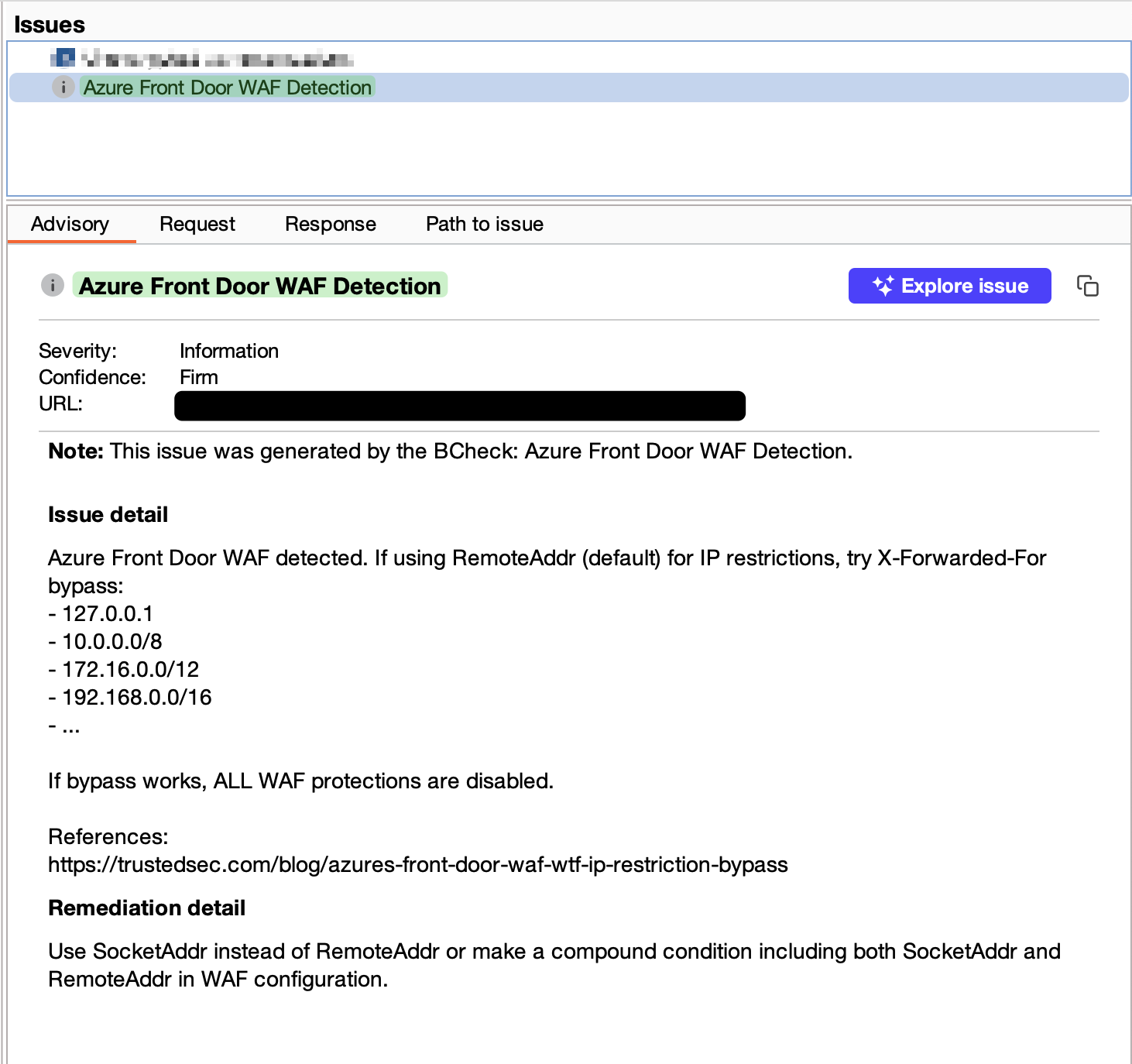
name: "Azure Front Door WAF Detection"
description: "Detects Azure Front Door WAF based on 403 response headers"
author: "fz42"
tags: "azure", "waf", "bypass"
given response then
if
{latest.response.status_code} is "403" and
{latest.response.headers} matches "(?i)x-azure-ref" and
{latest.response.headers} matches "(?i)x-cache"
then
report issue:
severity: info
confidence: firm
detail: `Azure Front Door WAF detected. If using RemoteAddr (default) for IP restrictions, try X-Forwarded-For bypass:
- 127.0.0.1
- 10.0.0.0/8
- 172.16.0.0/12
- 192.168.0.0/16
- ...
If bypass works, ALL WAF protections are disabled.
References:
https://trustedsec.com/blog/azures-front-door-waf-wtf-ip-restriction-bypass`
remediation: "Use SocketAddr instead of RemoteAddr or make a compound condition including both SocketAddr and RemoteAddr in WAF configuration."
end if
Now, I’ll have a nice reminder in Burp Suite ensuring I don’t miss this in the future.
Usage
Drop this into Burp’s BCheck editor. Every 403 response gets checked automatically.
Why this approach
I’ve collected 40+ bypass headers over the years (X-Forwarded-For, X-Real-IP, X-Client-IP, etc.). You can’t blast all of them at every 403 on a client engagement - that’s how you hit rate limits and get noticed.
This check identifies exactly when X-Forwarded-For will work (Front Door WAF with RemoteAddr). No spray and pray needed.
Between all the cloud providers and their quirks, I won’t remember that x-azure-ref + x-cache = Front Door WAF six months from now. But my BCheck will.
Last week I hit 4 WAF-protected endpoints. If any had been vulnerable Front Door configurations, this would’ve caught it automatically.